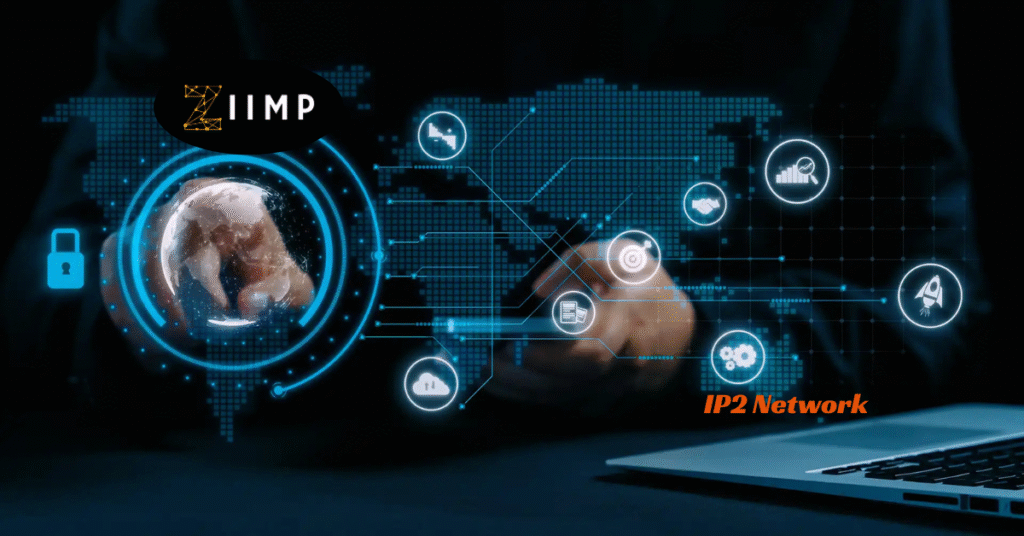
The digital world is growing more complex — with rising cyber‑attacks, privacy leaks, and increasing demands for control over personal data. IP2 Network 2025: Complete Guide to Online Security offers a fresh approach: a peer-to-peer, decentralized network that gives users more data control, stronger privacy, and resistance to common risks linked with centralized servers.
This article will explain what the IP2 Network is, how it works, what special features it provides, how you can set it up, and how it stacks up against traditional protocols or popular tools like VPN and Tor. It also looks at real‑world uses, potential limits, and whether this kind of network makes sense for you right now.
What Is IP2 Network?
IP2 Network represents a shift away from standard internet models. Rather than depending on central servers or fixed infrastructure, this concept relies on a mesh of connected devices — a node architecture — where each device can act as both client and server. In this model, data passes directly between peers. That means no single central authority is required to manage or route data, reducing reliance on a centralized point of control or failure.
This setup gives users more data sovereignty, letting them retain control over their own identity, communications, and storage. Because data isn’t stored or routed through corporate servers or centralized hubs, IP2 promises greater privacy, reduced exposure to third‑party surveillance, and more anonymity for people wanting secure, private communication.
As demand grows for decentralized apps, anonymous browsing, and protection against censorship or surveillance, IP2 Network aims to meet these needs. It can support encrypted messaging, file sharing, and P2P tunnels for private communication without intermediaries.
How IP2 Network Works: Technical Overview
Under the hood, IP2 Network uses principles from peer-to-peer networking. Each connected device — or “node” — contributes to the network, enabling a self‑healing network that spreads responsibilities for routing, storage, and bandwidth across many peers.
Because of this node architecture, the network avoids a single point of failure. If some nodes drop offline or are taken down, other nodes pick up the workload. That design brings network resilience: even with partial outages, the system stays functional.
Communication between peers uses encryption, meaning data transferred via the network is shielded against snooping or interception. This encryption can provide privacy and confidentiality.
Routing in IP2 is dynamic: instead of fixed, hierarchical paths like those in traditional IPv4 or IPv6 networks, data may take different routes based on availability, speed, and load. This smart routing and dynamic routing can reduce network latency and improve performance optimization when the network has enough peers.
Because each node offers its own resources — bandwidth, storage, computing — the network can scale organically as more users join. This scalability is one of the key strengths when demand increases.
In short, IP2 Network combines peer-to-peer connectivity with encryption, dynamic routing, and distributed resources to offer a flexible, resilient alternative to the centralized internet.
Key Features of IP2 Network
An IP2-style network offers several advantages that set it apart from traditional networks. First, its decentralized network structure delivers fault tolerance: no central server means fewer single points of failure. The network remains more robust even if some nodes drop offline.
Second, because each connected device contributes resources, IP2 enables scalability. As more nodes join, the total network capacity grows. That makes it suitable for growing user bases, large communities, or distributed applications.
Third, privacy and anonymity are central. Direct peer-to-peer connections, along with encryption, reduce reliance on intermediaries, guarding against centralized surveillance or data logging.
Fourth, performance benefits can arise: P2P networks often offer faster data transfer and better resource optimization, especially in scenarios like file sharing, media streaming, or content delivery, where many peers serve pieces of data.
Also, because the network doesn’t demand large infrastructure costs (no data centers, no massive servers), it can prove cost‑efficient. This efficiency can make services built on IP2 accessible to smaller organizations or projects without heavy budgets.
Because data is spread across multiple nodes, data redundancy and distributed storage become possible. That reduces the risk of loss or centralized data leaks.
Finally, this kind of network supports censorship resistance and information freedom, because it is harder for any single entity — government, ISP, corporation — to block or shut down the entire network when control is distributed.
You may also like this: Apple Teleport Explained: Real or Just Science Fiction?
Step-by-Step Setup Guide for IP2 Network
Getting started with IP2 Network requires installing compatible tools and configuring your device to use peer‑to‑peer routing rather than traditional centralized paths. Below is a general flow for setting it up.
Installing an IP2 Router
Begin by installing a router application or software that supports decentralized, peer‑to‑peer connections. This acts as the gateway bridging your device into the wider peer mesh. Once installed, grant the necessary permissions (network, port access) so the software can manage traffic through the peer network.
Using P2P Clients with Built-in IP2 Support
Choose applications (clients) that support peer-to-peer communication over the IP2 layer. For example, torrent clients or file‑sharing tools configured for P2P tunnels work well if they are set to route all traffic through the IP2 router — avoiding leaks to the regular internet. This helps maintain privacy, anonymity, and encrypted communication.
Configuring IP-over-P2P Tunnels
If supported, set up virtual tunnels (IP-over-P2P) that force your internet traffic through the peer network. This requires binding local ports to peer nodes, defining which applications use the tunnel, and ensuring data is encrypted before transmission. Such tunnels act like a decentralized VPN, giving you private, peer‑to‑peer connections.
Setting Up Applications to Use the IP2 Network
Once tunneling and routing are active, configure each application — web browser, messaging, file-sharing, streaming — to send all traffic through the IP2 network. After setup, test connectivity, latency, and stability. Verify that encryption works correctly and that data isn’t leaking through normal ISP routing.
Tips for Optimal IP2 Network Performance
To get the best out of IP2 Network, pick peers (nodes) with stable bandwidth and good uptime, and run software on devices with sufficient processing power. Poor peers or weak connections reduce overall performance. Regularly monitor the network — check latency, data flow, throughput, and peer reliability. Make sure encryption settings are up-to-date, and combine IP2 use with strong endpoint security.
Avoid depending solely on peer‑to‑peer tunnels for critical tasks unless the network seems stable and consistent. For important data transfers or sensitive applications, consider layering in additional protection (e.g., secure authentication, access controls). If your network supports Quality‑of‑Service (QoS), configure it to prioritize high‑priority traffic (video calls, streaming, real‑time communication) to reduce possible lags or interruptions.
IP2 Network vs Traditional Networks (IPv4/IPv6)
Traditional internet uses protocols like IPv4 or IPv6, relying on centralized infrastructure: ISPs, centralized servers, and data centers. Routing is hierarchical, and data flow depends on fixed paths. This model offers wide compatibility and consistent performance, but also concentrates risk: central servers can fail, be attacked, or be compromised.
By contrast, IP2’s decentralized network offers distributed routing, flexible topology, and peer-based resource sharing. Instead of fixed servers, many nodes handle traffic. That gives better resilience: the network continues even if many nodes fail. It also avoids dependence on centralized infrastructure, reducing vulnerability to server outages or large-scale attacks. Because of dynamic routing and resource sharing, IP2 can adapt to changes — ideally delivering lower latency and smoother data flow if enough peers participate.
However, compatibility depends on adoption. IPv4/IPv6 works globally out-of-the-box. IP2‑style networks require specialized clients and configurations. If few peers exist, performance and connectivity may suffer. Also, traditional networks are easier to manage and have standard protocols — IP2 requires reliable peer cooperation and configuration.
Key Differences Between IP2 Networks and Traditional Networks
IP2 shifts control and ownership from centralized entities to users. Instead of ISPs or servers controlling data and routing, each user owns their part of the network. This gives stronger data control and independence. The network becomes more resilient, since losing a few nodes doesn’t collapse the system. Privacy risks linked with centralized servers — like data logging or mass surveillance — are reduced because data moves directly between peers, often using encryption and IP obfuscation.
Scalability in IP2 is organic: every new node contributes resources, so the network grows naturally. Traditional networks require infrastructure upgrades for scaling, which can be costly. But IP2’s performance depends on peer participation; traditional protocols rely on stable physical infrastructure offering predictable performance.
You may also like this: Ultimate Workplace Management EWMagWork Guide 2025
IP2 Network vs VPNs, Tor, and Other Security Solutions
Comparing IP2 with VPNs and anonymization networks like Tor reveals interesting trade‑offs. VPNs protect traffic by routing it through a server, masking your IP, and encrypting your data. But they depend on a central provider’s trustworthiness: if that server is compromised or logs data, privacy is lost. Tor and similar networks use layers of routing to provide anonymity, but often at the cost of speed, reliability, or usability.
IP2 offers a different path: direct peer-to-peer connections, decentralized routing, and no reliance on any central server or centralized trust. That can reduce the risk of a single compromised server exposing user data. Because of decentralization, censorship resistance, and data sovereignty, IP2 could be more robust against server takedowns, mass logging, or centralized surveillance.
On the flip side, VPNs and Tor are mature, widely supported, and generally easier to use. They often offer stable performance and strong encryption. IP2 requires a sufficient network of reliable peers to reach similar levels of usability and performance. Without a good peer network, connections can be unstable, slow, or unreliable.
Benefits of Using IP2 Network for Online Security
Using IP2 Network gives you stronger control over your own data and identity. Because communication flows directly between peers, with optional encryption, you avoid many privacy risks associated with centralized servers and intermediaries. This makes IP2 appealing for private communication, sensitive file sharing, or any application requiring anonymity or data sovereignty.
The decentralized model also enhances network resilience. Outages affecting a subset of nodes or regions won’t necessarily impact the whole network. For communities, small organizations, or groups aiming for independence from big‑tech infrastructure, IP2 can provide a more democratic system of connectivity.
For content delivery, streaming, file sharing, or distributed storage, peer‑to-peer resource sharing offers cost efficiency, scalability, and redundancy. For applications in cloud computing, edge computing, or IoT devices, a decentralized network architecture offers flexibility that traditional centralized servers may struggle to provide — especially when demand spikes or global distribution is needed.
Real-World Applications of IP2 Network
IP2-style networks could support a wide variety of real-world uses. Encrypted messaging and anonymous browsing become possible without relying on centralized providers. Communities or platforms could build decentralized apps (social networks, file‑sharing services, private communication tools) that resist censorship or centralized control, even in restrictive regions. For users needing private file sharing or anonymous torrenting, peer-to-peer tunnels or clients can route traffic safely — with IP-over-P2P, P2P client tools, or similar solutions managing secure connections.
Organizations could leverage such networks for enterprise networking, remote collaboration, or secure data exchange — especially when traditional centralized servers pose a risk of data leaks or surveillance. Use cases in healthcare applications, telemedicine, finance, security, or government security might benefit from encrypted communication, data redundancy, and distributed storage, reducing single-point vulnerabilities.
For edge computing, IoT scalability, or smart cities, a decentralized network reduces dependency on central data centers. Devices spread across wide geographies could communicate directly, enabling real‑time applications, IoT data flow, and performance even with varying network conditions.
Challenges and Limitations of the IP2 Network
While the benefits are substantial, IP2‑style networks bring their own risks. Security remains a concern: because peers act independently, a malicious or compromised node could distribute malware, corrupt data, or launch attacks against other nodes. Without centralized oversight, verifying the trustworthiness of peers and maintaining consistent security standards across the network is difficult.
Performance and reliability can vary based on peer participation. If many nodes have weak bandwidth or poor connectivity, latency increases, data flow slows, and quality suffers — especially for high‑priority traffic like streaming or real‑time communication.
Management and usability challenges are significant, too. For non‑technical users, setting up a P2P client or configuring IP-over-P2P tunnels can be confusing. Without a central admin, user training and consistent configuration are necessary.
Legal or ethical issues may arise. Because P2P networks have been used for unauthorized file sharing or piracy, they sometimes attract scrutiny — and running a fully decentralized network may involve regulatory risks, depending on the region.
Finally, adoption matters. If only a small number of peers run the network, coverage will be limited. Low peer count weakens benefits like redundancy, scalability, speed, and resilience.
Future Trends and Developments in IP2 Network
The idea behind IP2 resonates with trends in decentralization, privacy, and distributed computing. As edge computing, IoT devices, and real-time applications become more common, decentralized networks may offer the flexibility that traditional infrastructure can’t match. For example, IoT scalability across devices, smart cities, and 5G compatibility could benefit from peer‑based routing and distributed resource sharing. If a hybrid infrastructure combining peer networks and traditional protocols emerges, users could get the best of both worlds — legacy support along with decentralized benefits.
Advances in cryptography, quantum computing, and decentralized identity systems may strengthen privacy and trust models for such networks. Decentralized finance (DeFi), decentralized storage, and secure communication — built on peer-to-peer mesh networks — could gain momentum if user-friendly tools and robust security measures become widely available.
Improvements in user experience, user-friendly apps, and easier network setup might make peer‑based networks more accessible to general users, not just technical experts. With wider adoption, decentralized networks could shift from niche to mainstream.
Is IP2 Network Worth It in 2025?
For people and organizations prioritizing privacy, data control, censorship resistance, and independence from centralized servers, IP2 Network provides a promising path. It offers meaningful advantages over traditional networks: greater anonymity, resilience, flexibility, and reduced reliance on central infrastructure.
However, it’s not a silver bullet. Risks with security, inconsistent performance, peer reliability, and legal concerns remain real. If you consider using IP2 for sensitive or critical tasks, it’s wise to combine it with good security practices, use trustworthy peers, and apply layered protections.
For early adopters, activists, privacy‑focused users, or small organizations exploring decentralized options, IP2 Network could be worth experimenting with in 2025. For mainstream users or large enterprises, it might serve best as part of a broader strategy rather than as a standalone solution.\
You may also like this: How TechoElite Smart Homes Transform Modern Living
Frequently Asked Questions (FAQs)
What is the IP2 Network?
IP2 Network is a peer-to-peer decentralized network that lets devices connect directly without relying on central servers. It offers encryption, privacy, and better data control.
How is IP2 Network different from traditional networks?
Answer: Unlike IPv4 or IPv6, which use centralized servers, IP2 uses a node architecture where each device helps route data. This improves resilience, scalability, and anonymity.
Can I use IP2 Network for secure messaging?
Yes, the network supports encrypted messaging apps, ensuring your communication remains private and hard to intercept.
Do I need special software to use IP2 Network?
Yes, you need IP2-compatible routers or P2P clients like I2PSnark, Tribler, or IPOP VPN to connect safely and manage traffic through the network.
Is IP2 Network faster than VPN or Tor?
It can be faster for real-time applications and streaming content because of smart routing and dynamic routing, though performance depends on the number and quality of active nodes.
Can IP2 Network help with anonymous browsing?
Yes, IP2 Network supports anonymous browsing by routing your connection through multiple peers and using IP obfuscation, which hides your identity online.
What types of applications work best on the IP2 Network?
IP2 works well for file sharing, media streaming, decentralized apps, enterprise networking, telemedicine, and other real-time applications needing low latency and encryption.
Is IP2 Network safe from cyberattacks?
It provides strong security with encryption, zero-trust frameworks, DDoS protection, and proactive threat detection, but combining it with VPNs or other security tools increases safety.
Can businesses benefit from IP2 Network?
Yes, organizations can use it for enterprise applications, cloud computing, finance security, healthcare applications, government security, and military communications, benefiting from scalability and redundancy.
Do I need training to use IP2 Network?
Some setup knowledge is helpful. Basic network setup, proxy manager configuration, IP binding, and monitoring skills ensure smooth performance and proper network latency management.
Conclusion
IP2 Network represents a shift away from centralized internet models toward a more open, peer-based, and user-controlled future. By distributing control, enabling encryption, and relying on dynamic routing, scalability, and decentralization, it offers new possibilities for privacy, resilience, and data autonomy. At the same time, its effectiveness depends heavily on adoption, peer reliability, and conscientious configuration. If you value privacy, anonymity, and freedom from centralized servers, IP2 Network could provide a strong foundation — especially when paired with secure practices and thoughtful planning.
✅ Stay updated with ziimp.net/blog for the latest tips, trending topics, and informative articles.
Disclaimer:
“This article is for educational purposes only and does not provide personal advice. Readers should research and consider risks before using IP2 Network or related technologies. The author is not responsible for any outcomes from its use.”
Author Profile
- I am the editor and publisher at Ziimp.net. I write clear and helpful content about credit cards, markets, technology, and trading. My focus is on simplifying finance and using smart tools to help readers make better decisions. I also explore new ideas to improve the platform and create a better experience for users.
Latest Posts
 FinanceDecember 13, 2025Indexationnews com Explained: Honest Guide to Finance & Loans
FinanceDecember 13, 2025Indexationnews com Explained: Honest Guide to Finance & Loans FinanceDecember 13, 2025AnalyzingMarket com Explained: Honest Insights & Reviews
FinanceDecember 13, 2025AnalyzingMarket com Explained: Honest Insights & Reviews TechnologyDecember 12, 2025SSIS 469 Error Explained: Ultimate Causes, Fixes, and Prevention
TechnologyDecember 12, 2025SSIS 469 Error Explained: Ultimate Causes, Fixes, and Prevention ReviewDecember 12, 2025Techmapz com Guide 2025: Full Comprehensive Platform Overview
ReviewDecember 12, 2025Techmapz com Guide 2025: Full Comprehensive Platform Overview